Introduction
Biometric security systems have become a vital part of modern security solutions. From unlocking smartphones to accessing high-security facilities, these systems use unique human characteristics to verify identity. Unlike traditional passwords or keycards, biometrics are difficult to duplicate, making them a powerful tool against fraud and unauthorized access.
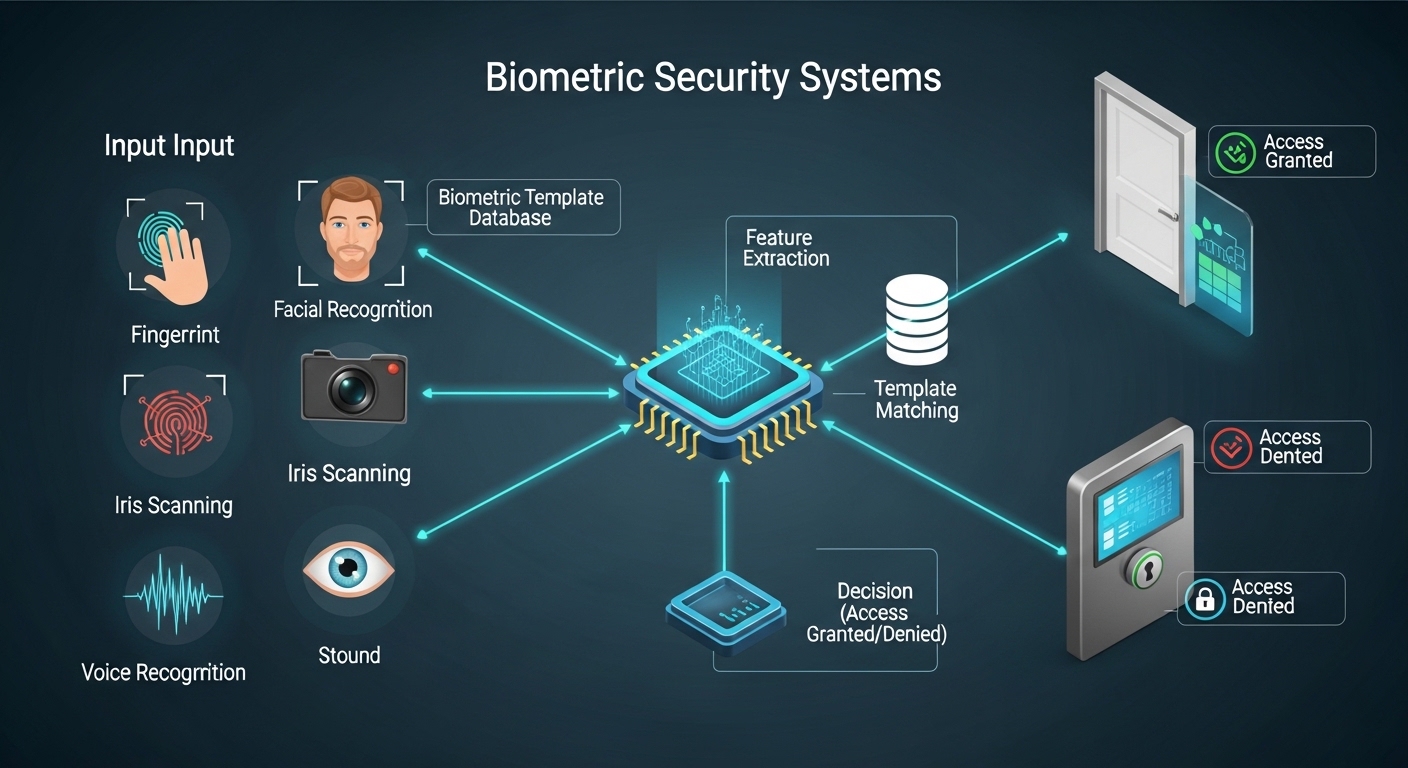
In this guide, we will explore how biometric security systems function, the technologies behind them, their benefits, and common applications.
What Are Biometric Security Systems?
Biometric security systems are authentication systems that rely on biological characteristics to identify individuals. These characteristics are unique to each person and can include:
-
Fingerprint patterns
-
Facial features
-
Iris and retina patterns
-
Voice recognition
-
Hand geometry
Instead of relying on something you know (like a password) or something you have (like a keycard), biometrics rely on who you are, making it inherently more secure.
How Biometric Systems Capture Data
Biometric systems function in two main steps: data capture and verification.
Step 1 – Enrollment
During enrollment, the system records a biometric sample from the user. Examples include:
-
Scanning a fingerprint with an optical or ultrasonic sensor
-
Capturing facial features using a camera
-
Scanning the iris using infrared light
The system converts these samples into digital templates. These templates are encrypted and stored in a secure database for future comparison.
Step 2 – Verification or Identification
When a user attempts access:
-
The system captures a new biometric sample
-
Compares it to the stored template using matching algorithms
-
Grants access if the match meets the system’s threshold of accuracy
Some systems operate in verification mode (1:1 match) while others use identification mode (1:N match against multiple stored profiles).
Types of Biometric Security Systems
Fingerprint Recognition
-
Most common biometric method
-
Scans ridges and valleys on a fingertip
-
Fast, cost-effective, and widely used in smartphones, laptops, and access control systems
Facial Recognition
-
Captures unique facial features such as the distance between eyes, nose shape, and jawline
-
Can operate in 2D or 3D for higher accuracy
-
Common in airports, smartphones, and surveillance systems
Iris and Retina Scanning
-
Uses patterns in the eye for authentication
-
Extremely precise but requires specialized sensors
-
Often used in high-security facilities and government systems
Voice Recognition
-
Analyzes vocal patterns
-
Can be used remotely over phone systems
-
Sensitive to background noise and voice changes
Hand Geometry
-
Measures the shape and size of a hand
-
Less unique than fingerprints or iris scans but useful in workplaces with controlled access
Benefits of Biometric Security Systems
-
Enhanced Security – Hard to replicate compared to passwords or cards
-
Convenience – Quick access without remembering codes
-
Accountability – Biometric logs can track user activity
-
Reduced Fraud – Difficult for unauthorized users to bypass
Limitations and Considerations
While biometric systems are powerful, they are not perfect:
-
False Acceptance Rate (FAR) – System may occasionally grant access to the wrong person
-
False Rejection Rate (FRR) – System may deny access to a legitimate user
-
Privacy Concerns – Biometric data is sensitive; breaches can be serious
-
Cost – Advanced systems like iris scanners are expensive
Proper encryption, system updates, and multi-factor authentication can mitigate these issues.
Common Applications
Biometric security systems are used in many industries:
-
Smartphones and laptops – Fingerprint and facial unlock
-
Airports and border control – Iris and facial scans
-
Financial services – Voice or fingerprint verification for transactions
-
Workplaces – Hand geometry or fingerprint time tracking
-
Healthcare – Secure access to patient records
Future Trends
Biometric technology continues to evolve:
-
Multimodal Biometrics – Combining two or more biometric types for higher accuracy
-
Behavioral Biometrics – Monitoring typing patterns, mouse movements, or gait
-
AI-Powered Recognition – Advanced algorithms increase speed and accuracy
-
Wearable Biometric Devices – Continuous authentication through smartwatches or fitness bands
These trends aim to improve security, convenience, and user experience in everyday technology.
Conclusion
Biometric security systems represent a modern, reliable, and user-friendly approach to authentication. By using unique human characteristics, these systems provide enhanced security and convenience across personal, professional, and government applications. Understanding how these systems function helps users appreciate the technology protecting their devices, data, and access points.
FAQ
Q1: Are biometric systems safer than passwords?
A1: Yes, because biometrics are unique and difficult to duplicate, making them more secure than traditional passwords.
Q2: Can biometric systems be hacked?
A2: While more secure than passwords, no system is completely invulnerable. Strong encryption and multi-factor authentication reduce risks.
Q3: What is the most common type of biometric security?
A3: Fingerprint recognition is the most widely used due to cost-effectiveness and ease of implementation.
Q4: Are biometric systems privacy-safe?
A4: When biometric data is encrypted and securely stored, it is safe. Privacy risks exist if systems are poorly managed.
